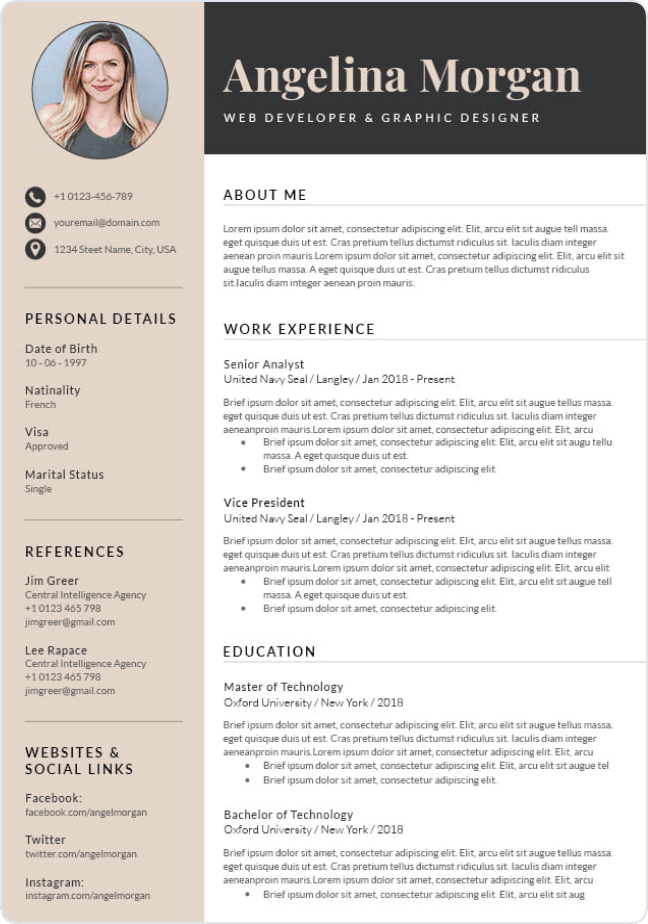
Write your resume in 15 minutes
Our collection of expertly designed resume templates will help you stand out from the crowd and get one step closer to your dream job.

This article breaks down the essential skills every cybersecurity specialist needs to thrive. It covers key technical abilities, critical soft skills, and the industry misconceptions that can hold professionals back.
The Skills Every Cybersecurity Specialist Needs
Cybersecurity specialists protect systems, detect threats, and respond to incidents. Their effectiveness depends on specific technical and strategic skills. Here’s what’s required to do the job well.

1. Scripting Skills
Scripting is the backbone of efficiency in cybersecurity. Knowing languages like Python, Bash, and PowerShell allows professionals to automate repetitive tasks, streamline processes, and analyze large datasets without manual intervention.
For example, instead of manually combing through thousands of log files to detect anomalies, a well-crafted script can flag suspicious patterns in seconds, enabling faster response times. Scripting also plays a critical role in intrusion detection systems, where automation helps identify threats in real time and triggers security measures without human delay.
2. Network Security
Network security focuses on securing data as it moves across systems and devices. This involves configuring firewalls, managing network security controls, setting up intrusion prevention systems, and using monitoring tools to detect unauthorized activity.
Cybersecurity professionals need to understand how data packets flow, how to segment networks to minimize attack surfaces, and how to spot vulnerabilities like open ports or weak encryption protocols. Strong network security reduces the risk of attacks such as distributed denial-of-service (DDoS), man-in-the-middle attacks, and unauthorized intrusions.
3. Operating Systems Expertise
A deep understanding of operating systems is essential because threats often exploit OS-level vulnerabilities. Cybersecurity specialists should be fluent in Windows, Linux, and macOS, with knowledge of system architecture, permissions, process management, and file systems.
This expertise helps in tasks like configuring secure environments, managing system updates to patch vulnerabilities, and conducting forensic analysis after security incidents. For example, knowing how to navigate Linux directories and read system logs can be the key to identifying the source of a breach.
4. Incident Response
Incident response is all about what happens after a breach or security incident occurs. It’s a structured approach to identifying, containing, eradicating, and recovering from cyber threats. Professionals with strong incident response skills can quickly assess the scope of an attack, determine the point of entry, and isolate affected systems to prevent further damage.
They also document the incident to analyze what went wrong and improve future response strategies. Effective incident response minimizes downtime, protects sensitive data, and ensures business continuity even under pressure.
5. Cryptography and Encryption
Cryptography is the science of securing information, and encryption is one of its most powerful tools. Cybersecurity professionals use encryption to protect data in transit (like emails or financial transactions) and data at rest (such as stored files or databases).
Techniques like Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA) algorithms ensure that even if data is intercepted, it remains unreadable without the proper decryption keys. Strong cryptographic practices are essential for compliance with security protocols and regulations like GDPR, HIPAA, and PCI-DSS.

6. Ethical Hacking
Ethical hacking, also known as penetration testing, is the practice of simulating cyberattacks to identify security weaknesses. Certified ethical hackers think like cybercriminals, using the same techniques; such as phishing, SQL injection, and brute force attacks, to find vulnerabilities before malicious actors do. This proactive approach helps organizations strengthen their defenses by addressing issues like outdated software, poor password practices, and misconfigured security settings. Ethical hacking isn’t about causing chaos; it’s about controlled, strategic testing to improve security.
7. Cloud Security
With businesses increasingly relying on cloud infrastructure, understanding cloud security is no longer optional. Cybersecurity professionals must know how to secure data stored in services like AWS, Azure, and Google Cloud. This includes managing identity and access controls, ensuring proper configuration of cloud resources, and monitoring for unauthorized activity.
Misconfigurations in cloud environments are a leading cause of data breaches, making cloud security skills critical for preventing accidental exposure of sensitive information.
8. Malware Analysis
Malware analysis is the process of dissecting malicious software to understand how it works, how it spreads, and how to stop it. This involves both static analysis (examining code without running it) and dynamic analysis (observing how malware behaves in a controlled environment).
Understanding malware is key to improving detection methods, strengthening intrusion detection systems, and developing better malware prevention strategies. For example, analyzing ransomware code can reveal encryption techniques used by attackers, helping teams develop decryption tools and recovery methods.
9. Risk Management
Risk management is about identifying potential threats, assessing their likelihood and impact, and implementing strategies to mitigate them. This includes conducting regular security assessments, developing threat models, and prioritizing vulnerabilities based on the level of risk they pose.
Effective risk management helps organizations allocate resources wisely, focusing on the most critical security measures to reduce exposure to cyber threats. It also plays a key role in compliance with regulatory guidelines and industry standards.
10. Security Protocols
Security protocols are the rules and procedures that govern secure communication across networks. Protocols like SSL/TLS (for secure web browsing), IPsec (for encrypted network traffic), and HTTPS (for secure websites) help protect data from interception and tampering.
Cybersecurity professionals need to understand how these protocols work, how to configure them securely, and how to identify weaknesses that could be exploited. Strong protocol management ensures data integrity, confidentiality, and authentication in all digital transactions.
The Soft Skills That Set Cybersecurity Professionals Apart
Cybersecurity professionals deal with unpredictable threats, shifting technologies, and high-stakes decisions where technical skills alone aren’t enough. The ability to think critically, work seamlessly with others, and make smart calls under pressure turns knowledge into action.

1. Clear Communication
Explaining complex security issues in simple terms is critical. Cybersecurity professionals often need to brief executives, train staff, or write reports that influence key decisions. Strong communication bridges the gap between technical details and business priorities.
2. Team Collaboration
Cybersecurity relies on teamwork across departments. Professionals coordinate with IT, legal, compliance, and management to develop security strategies, handle incidents, and implement security protocols. Strong collaboration ensures faster, more effective responses to threats.
3. Attention to Detail
Overlooking small issues can lead to major security breaches. Attention to detail helps professionals spot anomalies in system logs, detect subtle vulnerabilities, and ensure precise configurations. This focus reduces the risk of critical errors that attackers can exploit.
4. Critical Thinking
Every security incident presents unique challenges. Critical thinking allows professionals to assess situations quickly, identify potential risks, and develop effective solutions. This skill is key when evaluating threats that don’t follow a predictable pattern.
5. Problem-Solving Under Pressure
Security incidents rarely come with advance notice. Problem-solving skills help professionals stay calm, analyze situations, and make fast decisions when systems are compromised. The ability to think clearly under pressure can prevent a minor issue from escalating into a major breach.

6. Risk Assessment
Identifying risks is the first step; evaluating their potential impact is what drives smart decisions. Risk assessment skills help cybersecurity professionals prioritize threats, allocate resources effectively, and reduce vulnerabilities across systems.
7. Adaptability
The cybersecurity landscape shifts constantly with new threats, technologies, and regulations. Adaptability allows professionals to pivot quickly, learn new tools, and adjust strategies to stay ahead of evolving risks.
8. Ethical Judgment
Handling sensitive data and critical systems requires strong ethical standards. Cybersecurity professionals must make decisions that protect privacy, maintain integrity, and uphold security best practices, even under pressure.
9. Leadership Skills
Leadership isn’t limited to formal titles. Cybersecurity professionals often lead incident response efforts, guide teams during crises, and influence security strategies. Strong leadership skills help coordinate actions, delegate tasks, and build confidence within teams.
10. Curiosity and Continuous Learning
Curiosity drives professionals to explore new threats, experiment with security tools, and stay informed about emerging trends. Continuous learning keeps skills sharp, fosters innovation, and helps anticipate threats before they become critical issues.
How to Build and Sharpen Cybersecurity Skills
Cybersecurity demands practical, hands-on experience backed by continuous learning. Here’s exactly how to build the technical and soft skills that matter in this field.

1. Build a Home Lab for Hands-On Practice
A home lab is the best place to experiment, break things safely, and understand how systems respond to real attacks. Use tools like VirtualBox or VMware to set up virtual machines running different operating systems; Windows Server, Kali Linux, and Ubuntu are a solid start. Practice configuring firewalls, running vulnerability scans with Nmap, and simulating attacks using Metasploit. This setup lets you test intrusion detection systems, analyze logs, and sharpen incident response strategies without risking real-world networks.
2. Master Networking and System Administration
Strong cybersecurity skills are built on a foundation of networking and system administration. Learn how data moves through networks by studying TCP/IP, setting up DNS servers, and configuring routers using Cisco Packet Tracer. Dive into system administration by managing Linux permissions, automating tasks with Bash scripts, and securing Windows environments with Group Policy Objects (GPOs). Understanding how systems operate makes it easier to detect when something isn’t right.
3. Focus Deeply on One Technical Skill at a Time
Trying to learn everything at once leads to shallow knowledge. Choose a focus; like intrusion detection systems, and dive deep. Install tools like Snort or Suricata, simulate attacks (brute force, SQL injection), and fine-tune detection rules. Analyze how traffic patterns change during attacks and adjust configurations to reduce false positives. Mastering one skill thoroughly provides a strong base to build on.
4. Earn Certifications That Align with Real Skills
Certifications can structure your learning and prove your expertise, but they should reflect hands-on ability, not just test-taking skills. Start with CompTIA Security+ for foundational knowledge, then pursue specialized certifications like OSCP for penetration testing or AWS Certified Security – Specialty for cloud security. Use certification objectives as a roadmap, pairing study with practical exercises in your home lab to ensure you can apply what you’ve learned.
5. Simulate Security Incidents and Learn from Failures
Experience comes from doing, and failing. Create vulnerable environments using tools like Metasploitable or DVWA (Damn Vulnerable Web App). Launch controlled attacks, then shift into defense mode: trace the breach, analyze logs, and document the attack lifecycle. Identify what security measures failed and adjust your defenses. This process builds critical incident response skills and shows how real-world attacks unfold.
6. Engage with Cybersecurity Communities
You can’t learn cybersecurity in isolation. Join communities like Reddit’s r/netsec, Stack Exchange’s Information Security forum, or local DEF CON groups to exchange knowledge, discuss emerging threats, and collaborate on projects. Participate in Capture The Flag (CTF) competitions to solve real-world security challenges in a team environment. Networking with other professionals exposes you to different tools, techniques, and career opportunities while keeping your skills sharp.

Conclusion
Cybersecurity is a dynamic field that thrives on curiosity, critical thinking, and hands-on problem-solving. The skills covered here are practical tools designed to help you outsmart evolving threats and stay ahead in a fast-paced industry. Keep learning, stay sharp, and approach every challenge with a mindset focused on growth and resilience.